Collections Cybersecurity Collection Cisco ITPro.TV - Understanding Cisco Cybersecurity Fundamentals
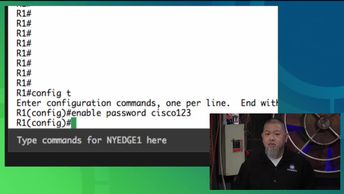
Explore how crypto algorithms are used to help secure data in a digital environment, including the use of hash and encryption algorithms. Discover the differences between symmetric and asymmetric key encryption and when to use each.
| Objectives |
|---|
SECFND: Cryptography
|