IT Skills Security Security Accreditations and Best Practice Certified Ethical Hacker (CEH) v10
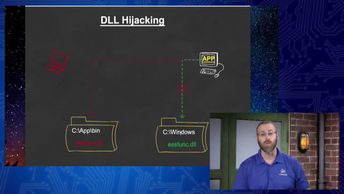
Explore multiple methods to hijack or use insecure configurations to gain unauthorized privileges, as you prepare for the 312-50: Certified Ethical Hacker v10 exam. Watch these videos and learn how to describe the different types of privilege escalation, create a malicious executable with Kali Linux to elevate privileges, and describe how to work with schedule tasks. You will also observe how to use command parameters to elevate privileges, locate an exploit in Kali Linux, compile source code into an executable program, and use Metasploit to exploit a Windows system.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: Privilege Escalation
|