IT Professional Curricula Internet and Network Technologies Solution Area Security Solutions Certified Ethical Hacker (CEH) v10
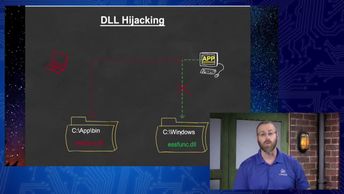
Explore multiple methods to hijack, or use insecure configurations, to gain unauthorized privileges.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: Privilege Escalation
|