Certification EC-Council Certified Ethical Hacker (CEH) Certified Ethical Hacker v10
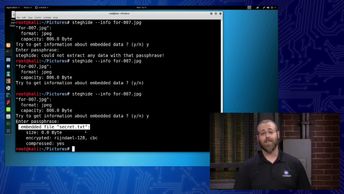
Discover the necessity of hiding files and the use of alternate data streams and steganography as tactics for hiding information. Explore how to cover tracks after breaching a system, including disabling auditing systems and clearing logs.
| Objectives |
|---|
CEHv10: Hidden Files and Covering Tracks
|