IT Skills Security Security Accreditations and Best Practice Certified Ethical Hacker (CEH) v10
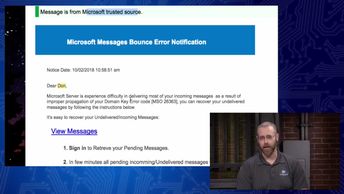
Discover how social engineering manipulates trust to elicit information from targets through emotional responses and other tactics, as you prepare for the 312-50: Certified Ethical Hacker v10 exam. Watch these videos and recognize hacking tactics to gain access through secure areas. See how shoulder surfing works as a form of social engineering. Describe a framework for a social engineering tool in Kali. Postulate a method of attack on a specific user in a high-level position. Show how phishing can compromise business email accounts. Conclude by learning how to identify malicious techniques that harvest user information from a mobile device.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: Social Engineering
|