IT Skills Security Security Accreditations and Best Practice Certified Ethical Hacker (CEH) v10
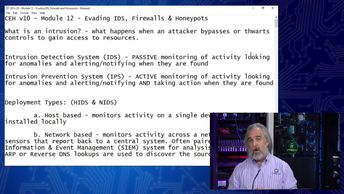
Explore how to evade intrusion detection systems, firewalls, and honeypots. Examine the use of Nmap to evade firewalls and how to set up a honeypot.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: Evading IDS, Firewalls, and Honeypots
|