IT Skills Security Security Accreditations and Best Practice Certified Ethical Hacker (CEH) v10
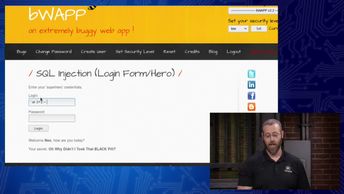
Explore SQL Injection attacks and how they can be used to inject, retrieve, or bypass authentication mechanisms.
| Objectives |
|---|
CEHv10: SQL Injection
|