IT Professional Curricula Internet and Network Technologies Solution Area Security Solutions Certified Ethical Hacker (CEH) v10 (Update)
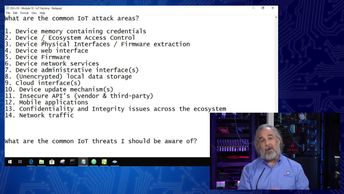
Discover the vulnerabilities and attacks that can lead to IoT systems being compromised, as you prepare for the 312-50: Certified Ethical Hacker v10 exam. Watch these videos and learn how to identify the top IoT vulnerability, describe the first action to secure a device, identify common IoT attack areas, describe the top three IoT threats, define the type of attack that involves your device in a botnet, list the steps of an IoT hacking methodology, and identify the tools used to perform IoT attacks.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: IoT Attacks
|