IT Professional Curricula Internet and Network Technologies Solution Area Security Solutions Certified Ethical Hacker (CEH) v10 (Update)
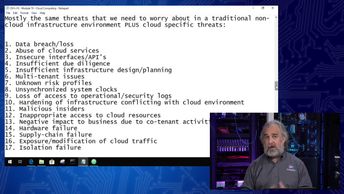
Explore the vulnerabilities and attacks that can lead to cloud systems being compromised, as you prepare for the 312-50: Certified Ethical Hacker v10 exam. Watch these videos and learn how to describe cloud computing threats that involve using the cloud services within the attack, follow best practices with time and logging within the cloud, recognize common cloud computing attacks, describe the cloud attack that translates SOAP messages, define the cloud attack that involves placing the attackerâs synchronization token on the userâs system, and list the OWASP Top 10 Application Security Risks.
| Objectives |
|---|
Certified Ethical Hacker - CEHv10: Cloud Computer Attacks
|